What is AWS KMS?
AWS Key Management Service (KMS) makes it simple for you to make and oversee cryptographic keys and control their utilization over a wide scope of AWS administrations and in your applications. AWS KMS is a safe and tough help that utilizes equipment security modules that have been approved under FIPS 140-2, or are being approved, to ensure your keys. AWS KMS is incorporated with AWS CloudTrail to give you logs of all key use to help meet your administrative and consistent needs.

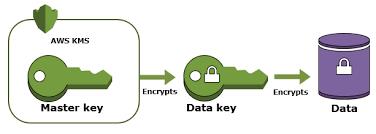
AWS Key Management Service (KMS) gives you brought together authority over the cryptographic keys used to secure your information. The administration is incorporated with different AWS administrations making it simple to encode the information you store in these administrations and control access to the keys that unscramble it. AWS KMS is incorporated with AWS CloudTrail, which gives you the capacity to review who utilized which keys, on which assets, and when. AWS KMS empowers designers to effectively include encryption or advanced mark usefulness to their application code either straightforwardly or by utilizing the AWS SDK. The AWS Encryption SDK underpins AWS KMS as an ace key supplier for designers who need to scramble/decode information locally inside their applications.
Unified Key Management
AWS KMS furnishes you with unified authority over the lifecycle and authorizations of your keys. You can make new keys at whatever point you wish, and you can control who can oversee keys versus who can utilize them. As an option in contrast to utilizing keys created by AWS KMS, you can import keys from your own key administration framework, or use keys put away in your AWS CloudHSM bunch. You can pick the programmed pivot of ace keys created in AWS KMS once every year without the need to re-encode recently scrambled information. The administration consequently keeps more seasoned adaptations of the ace key accessible to unscramble recently scrambled information. You can deal with your lord keys and review their use from the AWS Management Console or by utilizing the AWS SDK or AWS Command Line Interface (CLI).
* The alternative to import keys isn't accessible for Asymmetrickeys.
AWS Service Integration
AWS KMS is consistently coordinated with most AWS administrations. These incorporations use envelope encryption, where an information encryption key utilized by the AWS administration to encode your information is secured under a client ace key (CMK) put away in AWS KMS. There are two sorts of CMKs: (I) an AWS oversaw CMK that is made naturally when you initially make an encoded asset in an AWS administration. You can follow the use of an AWS oversaw CMK, yet the lifecycle and authorizations of the key are overseen for your sake. (ii) a client oversaw CMK that no one but you can make. Client oversaw CMKs give you full power over the lifecycle and consents that figure out who can utilize the key and under which conditions.
Review Capabilities
In the event that you have AWS CloudTrail empowered for your AWS account, each solicitation you make to AWS KMS is recorded in a log document that is conveyed to the Amazon S3 basin that you determined when you empowered AWS CloudTrail. The data recorded incorporates subtleties of the client, time, date, API activity, and, when applicable, the key utilized.
Adaptability, Durability, and High Availability
AWS KMS is a completely overseen administration. As your utilization of encryption develops, the administration naturally scales to address your issues. It empowers you to oversee a large number of CMKs in your record and to utilize them at whatever point you need. It characterizes default limits for the number of keys and solicitation rates, however, you can demand expanded cutoff points if important.
The CMKs you make or ones that are made for your sake by different AWS administrations can't be traded from the administration. Consequently, AWS KMS assumes liability for its solidness. To help guarantee that your keys and your information are profoundly accessible, it stores various duplicates of encoded adaptations of your keys in frameworks that are intended for 99.999999999% toughness.
On the off chance that you import keys into the administration, you keep up a protected duplicate of the CMKs with the goal that you can re-import them on the off chance that they are not accessible when you have to utilize them. On the off chance that you utilize the custom key store highlight to make your CMKs in an AWS CloudHSM group, encoded duplicates of your keys are naturally upheld up and you have full authority over the recuperation procedure.
AWS KMS is intended to be a profoundly accessible help with a territorial API endpoint. As most AWS administrations depend on it for encryption and unscrambling, it is architected to give a degree of accessibility that bolsters the remainder of AWS and is upheld by the AWS KMS Service Level Agreement.
Secure
AWS KMS is structured with the goal that nobody, including AWS workers, can recover your plaintext keys from the administration. The administration utilizes equipment security modules (HSMs) that have been approved under FIPS 140-2, or are being approved, to ensure the privacy and respectability of your keys. This it genuine whether or not you demand AWS KMS to make keys for your sake, make them in an AWS CloudHSM bunch, or import them into the administration. Your plaintext keys are never composed to circle and just at any point utilized in the unstable memory of the HSMs for the time expected to play out your mentioned cryptographic activity. Keys made by the administration AWS KMS are never transmitted outside of the AWS area wherein they were made and must be utilized in the district in which they were made. Updates to the AWS KMS HSM firmware is constrained by multi-party get to control that is evaluated and surveyed by a free gathering inside Amazon just as a NIST authorize lab in consistence with FIPS 140-2.
Custom Key Store
AWS KMS gives the alternative to you to make your own key store utilizing HSMs that you control. Every custom key store is sponsored by an AWS CloudHSM group. At the point when you make a CMK in a custom key store, the administration produces and stores key material for the CMK in an AWS CloudHSM bunch that you possess and oversee. At the point when you utilize a CMK in a custom key store, the cryptographic activities under that key are acted in your AWS CloudHSM group.
CMKs put away in a custom key store are overseen by you like some other CMK and can be utilized with any AWS administration that incorporates with AWS KMS.
The utilization of a custom key store includes the extra expense of the AWS CloudHSM group and makes you answerable for the accessibility of the key material in that bunch. For direction on whether custom key stores are a solid match for your necessities, you can peruse this blog.
* The Custom Key Store highlight isn't accessible in the AWS China (Beijing) Region, worked by Sinnet and the AWS China (Ningxia) Region, worked by NWCD.
** The Custom Key Store alternative isn't accessible for Asymmetric MKs.
Asymmetric Keys
AWS KMS gives you the ability to make and utilize Asymmetric CMKs and information key sets. You can assign a CMK for use as a marking key pair or an encryption key pair. Key pair age and awry cryptographic tasks utilizing these CMKs are performed inside HSMs. You can demand the open bit of the awry CMK for use in your nearby applications, while the private segment never leaves the administration.
You can likewise demand the administration to create a deviated information key pair. This activity restores a plaintext duplicate of the open key and private key just as a duplicate of the private key encoded under asymmetric CMK that you determine. You can utilize the plaintext open or private key in your neighborhood application and store the scrambled duplicate of the private key for sometime later.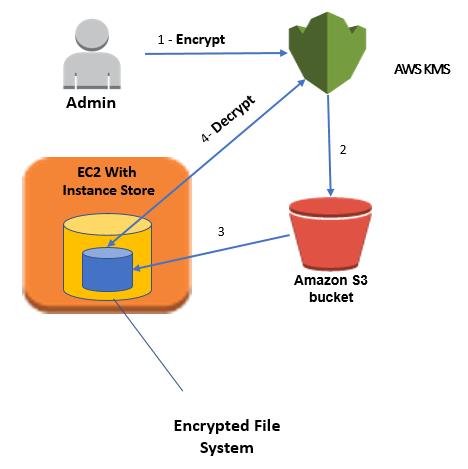
Advantages
Completely manageable
You control access to your encoded information by characterizing consents to utilize keys while AWS KMS implements your authorizations and handles the strength and physical security of your keys.
Concentrated key administration
AWS KMS presents a solitary control point to oversee keys and characterize strategies reliably across incorporated AWS administrations and your own applications. You can without much of a stretch make, import, pivot, erase, and oversee authorizations on keys from the AWS Management Console or by utilizing the AWS SDK or CLI.
Oversee encryption for AWS administrations
AWS KMS is coordinated with AWS administrations to rearrange utilizing your keys to encode information over your AWS remaining tasks at hand. You pick the degree of access control that you need, including the capacity to share encoded assets among records and administrations. KMS logs all utilization of keys to AWS CloudTrail to give you a free perspective on who got to your encoded information, including AWS administrations utilizing them for your benefit.
Scramble information in your applications
AWS KMS is incorporated with the AWS Encryption SDK to empower you to utilized KMS-secured information encryption keys to encode locally inside your applications. Utilizing basic APIs you can likewise manufacture encryption and key administration into your own applications any place they run.
Carefully sign information
AWS KMS empowers you to perform advanced marking activities utilizing awry key sets to guarantee the trustworthiness of your information. Beneficiaries of carefully marked information can confirm the marks whether they have an AWS account or not.
Ease
There is no dedication and no forthright charges to utilize AWS KMS. You just compensation US $1/month to store any key that you make. AWS oversaw keys that are made for your benefit by AWS administrations are allowed to store. You are charged per-demand when you utilize or deal with your keys past the complementary plan.
Secure
AWS KMS utilizes equipment security modules (HSMs) that have been approved under FIPS 140-2, or are being approved, to produce and ensure keys. Your keys are just utilized inside these gadgets and can never leave them decoded. KMS keys are never shared outside the AWS district in which they were made.
Consistence
The security and quality controls in AWS KMS have been ensured under various consistent plans to streamline your own consistent commitments. AWS KMS gives the alternative to store your keys in single-occupant HSMs in AWS CloudHSM cases that you control.
Worked in inspecting
AWS KMS is incorporated with AWS CloudTrail to record all API demands, including key administration activities and use of your keys. Logging API demands causes you to oversee chance, meet consistent necessities, and direct scientific investigation.