What is AWS CLI
AWS Command-line Interface (AWS CLI) is basically a tool which makes user capable of interacting with AWS services using commands. It is an open-source tool with a command-line shell and minimal configuration. AWS CLI allows you to run commands that are functionally equivalent to the browser-based AWS management console from the command-line shell in any terminal program:

Linux shells – Use normal shell projects, for example, bash, zsh, and tcsh to run commands in Linux or macOS.
Windows command line – On Windows, run commands at the Windows command prompt or in PowerShell.
Remotely – Run commands on Amazon Elastic Compute Cloud (Amazon EC2) occurrences through a remote terminal program, for example, PuTTY or SSH, or with AWS Systems Manager.
The AWS CLI is accessible in two forms and data in this guide applies to the two adaptations except if expressed something else.
Version 2.x – The current, for the most part, accessible arrival of the AWS CLI that is expected to use underway conditions. This version incorporates some "breaking" changes from version 1 that may expect you to change your scripts with the goal that they keep on working as you anticipate. For a rundown of new highlights and breaking changes in version 2, see Breaking changes – Migrating from AWS CLI version 1 to version 2.
Version 1.x – The past version of the AWS CLI is accessible for in reverse similarity.
All IaaS (framework as a help) AWS organization, the board, and access capacities in the AWS Management Console are accessible in the AWS API and CLI. New AWS IaaS highlights and administrations give full AWS Management Console usefulness through the API and CLI at dispatch or inside 180 days of dispatch.
The AWS CLI gives direct access to the open APIs of AWS administrations. You can investigate an assistance's capacities with the AWS CLI, and create shell scripts to deal with your assets. Or then again, you can take what you figure out how to create programs in different dialects by utilizing the AWS SDKs. Notwithstanding the low-level, API-identical orders, a few AWS administrations give customizations to the AWS CLI. Customizations can incorporate more elevated level orders that disentangle utilizing help with an unpredictable API.
Using AWS CLI:
Command Structure:
The AWS Command Line Interface (AWS CLI) utilizes a multipart structure on the order line that must be determined in a specific order:
![]()
The base call is made to the AWS program.
Next comes the high-level command. This command corresponds to AWS service.
The subcommand indicates which activity to perform.
General CLI choices or boundaries required by the activity. You can indicate these in any request as long as they follow the initial three sections. In the event that a restrictive boundary is indicated on numerous occasions, just the last worth applies.
Boundaries can take different sorts of information esteems, for example, numbers, strings, records, guides, and JSON structures. What is upheld is reliant upon the order and subcommand you determine.
Specifying parameters:
Numerous boundaries utilized in the AWS Command Line Interface (AWS CLI) are basic string or numeric qualities, for example, the key-pair name my-key-pair in the accompanying model.

You can encompass strings that don't contain any space characters with quotes or not. In any case, you should utilize quotes around strings that incorporate at least one space character.
Types of parameters:
This segment portrays a portion of the normal boundary types and the ordinary required configuration. On the off chance that you are experiencing difficulty designing a boundary for a particular order, check the assistance by entering help after the order name, as appeared.
String
String boundaries can contain alphanumeric characters, images, and blank areas from the ASCII character set. Strings that contain void areas must be encircled by quotes. We suggest that you don't utilize images or blank areas other than the standard space character since it can cause sudden outcomes.
Some string boundaries can acknowledge parallel information from a record. See Binary records for a model.
Timestamp
Timestamps are designed by the ISO 8601 norm. These are once in a while alluded to as "DateTime" or "Date" boundaries.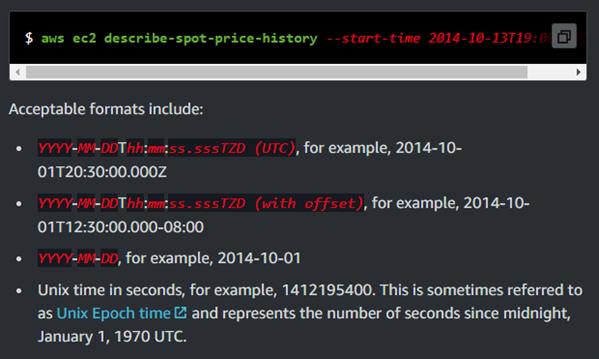
List:
In lists, strings are separated is used and are separated by space. A quotation mark is mandatory to be used after space.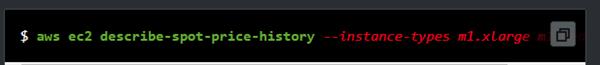

Boolean:
Boolean, the same as in any other language, acts as a flag with only two options “on” and “off”.
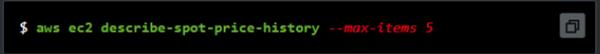
Integer:
Integers are the unsigned, whole numbers.
Binary Large Object:
It is a varying length binary string that can hold long characters. In version 1, the path to a local file that contains the data must be specified to pass the value to the parameter. The path should be free from protocol identifiers like https:// or file://. The path will be interpreted as a part of the current directory. For example,
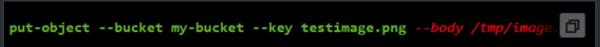
It is a BLOB object.
In version 2, Base64 encoded string can be passed on the command line. Secondly files with prefix like file:// are treated as base64 encoded text by default.
Map:
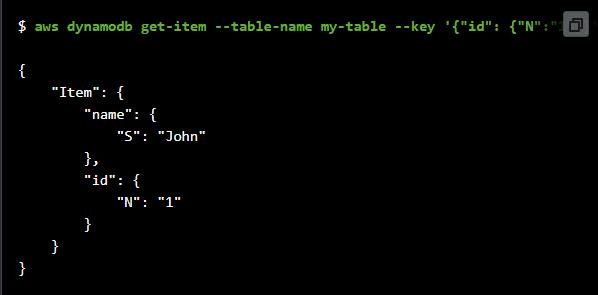
A lot of key-value sets determined in JSON or by utilizing the CLI's shorthand sentence structure. The accompanying JSON model peruses a thing from an Amazon DynamoDB table named my-table with a guide boundary, - key. The boundary determines the essential key named id with a number estimation of 1 of every a settled JSON structure.
Security in the AWS Command Line Interface
Cloud security at AWS is the most elevated need. As an AWS client, you profit by a server farm and system design that is worked to meet the necessities of the most security-delicate associations.
Security is a mutual obligation among AWS and you. The mutual duty model depicts this as security of the cloud and security in the cloud:
Security of the cloud – AWS is answerable for ensuring the framework that runs AWS administrations in the AWS Cloud. AWS additionally gives you benefits that you can utilize safely. Outsider examiners consistently test and check the adequacy of our security as a major aspect of the AWS Compliance Programs. To find out about the consistency in the programs that apply to AWS Command Line Interface, see AWS Services in Scope by Compliance Program.
Security in the cloud – Your duty is dictated by the AWS administration that you use. You are likewise liable for different variables including the affectability of your information, your organization's necessities, and relevant laws and guidelines.
Data protection:
For information security purposes, we suggest that you ensure AWS account certifications and set up singular client accounts with AWS Identity and Access Management (IAM), so every client is given just the authorizations important to satisfy their activity obligations. We likewise suggest that you secure your information in the accompanying manners:
Use Multi-Factor Authentication (MFA) with each record.
Use SSL/TLS to speak with AWS assets.
Set up API and client action logging with AWS CloudTrail.
Use AWS encryption arrangements, alongside all default security controls inside AWS administrations.
Utilize progressed oversaw security administrations, for example, Amazon Macie, which helps with finding and making sure about close to home information that is put away in Amazon S3.
Identity and Access Management for the AWS CLI:
The AWS Command Line Interface (AWS CLI) utilizes similar clients and jobs to get to your AWS assets and their administrations. The arrangements that award consents are the equivalent on the grounds that the AWS CLI considers similar API activities that are utilized by the administration comfort. For more data, see the "Personality and Access Management" segment in the "Security" section of the AWS administration that you need to utilize.
The main significant distinction is the means by which you validate when utilizing a standard IAM client and long haul accreditations. Albeit an IAM client requires a secret word to get to an AWS administration's comfort, that equivalent IAM client requires an entrance key pair to play out similar tasks utilizing the AWS CLI. All other momentary accreditations are utilized similarly they are utilized with the reassuring.