What is Amazon GuardDuty | AWS GuardDuty
Amazon GuardDuty
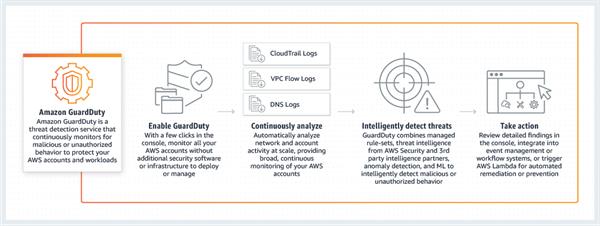
Amazon GuardDuty is a continuous security monitoring service that investigates and processes the accompanying data sources: VPC Flow Logs, AWS CloudTrail event logs, and DNS logs. It utilizes threat intelligence feeds, for example, a list of malicious IP locations and domains, and AI to distinguish expected and potentially unapproved and malicious action inside your AWS environment. This can incorporate issues like accelerations of benefits, uses of exposed credentials, or communication with malicious IP addresses, URLs, or domains. For instance, GuardDuty can identify traded off EC2 instances serving malware or mining bitcoin. It additionally screens AWS account get to conduct for indications of compromise, for example, unapproved foundation organizations, similar to occurrences conveyed in a Region that has never been utilized, or uncommon API calls, like a password policy change to reduce password strength.

GuardDuty informs you of the status of your AWS environment by producing security findings that you can view in the GuardDuty console or through Amazon CloudWatch events.
Benefits
Comprehensive threat identification
GuardDuty recognizes dangers by consistently checking the network action and record conduct inside the AWS condition. Amazon GuardDuty comes coordinated with exceptional danger knowledge takes care of from AWS, CrowdStrike, and Proofpoint. Threat intelligence combined with AI and conduct models assist you with identifying action, for example, digital money mining, certification bargain conduct, correspondence with known order and-control servers, or API calls from known malicious IPs.
Strengthens security through automation
In addition to detecting threats, GuardDuty additionally makes it simple to mechanize how you react to dangers, diminishing your remediation and recuperation time. GuardDuty can perform computerized remediation activities by utilizing Amazon CloudWatch occasions and AWS Lambda. GuardDuty security findings are informative and actionable for security operations, findings include the affected resource’s details and attacker information, such as IP address and geo-location.
Enterprise-scale and central management
GuardDuty makes enablement and the management over different records simple. Through the multi-account include, all part accounts discoveries can be amassed with a GuardDuty head account. This empowers the security group to deal with all GuardDuty discoveries from over the association in one single record. The totaled discoveries are likewise accessible through CloudWatch Events, making it simple to incorporate with a current undertaking occasion the executive's framework.
Features
Accurate, account-level threat detection
Amazon GuardDuty gives you threat detection of account compromise which can be especially hard to distinguish rapidly on the off chance that you are not continuously observing for factors in near real-time. GuardDuty can recognize indications of account compromise, for example, access to AWS resources from an unordinary geo-area at an atypical time of day. For automatic AWS accounts, GuardDuty checks for irregular API calls, for example, endeavors to darken account movement by debilitating CloudTrail logging or taking previews of a database from a malicious IP address.
Continuous monitoring across AWS accounts without added cost and complexity
Amazon GuardDuty constantly monitors and breaks down your AWS account and remaining workload event data found in AWS CloudTrail, VPC Flow Logs, and DNS Logs. There is no extra security programming or foundation to send and keep up. By partner your AWS accounts together you can total danger location as opposed to chipping away at a record by-account premise. Furthermore, you don't need to gather, break down, and correspond huge volumes of AWS data from various records. So, you can focus on how to respond quickly, how to keep your organization secure, and continuing to scale and innovate in the AWS Cloud.
Threat severity levels for efficient prioritization
Amazon GuardDuty provides three severity levels (Low, Medium, and High) to help customers prioritize their response to potential threats. A “Low” severity level indicates a suspicious or malicious activity that was blocked before it compromised your resource. A “Medium” severity level indicates suspicious activity. For example, a large amount of traffic being returned to a remote host that is hiding behind the Tor network, or activity that deviates from normally observed behavior. A “High” severity level indicates that the resource in question (e.g. an EC2 instance or a set of IAM user credentials) is compromised and is actively being used for unauthorized purposes.
Automate threat response and remediation
Amazon GuardDuty offers HTTPS APIs, CLI tools, and AWS CloudWatch Events to support automated security responses to security findings. For example, you can automate the response workflow by using CloudWatch Events as an event source to trigger an AWS Lambda function.
Highly available threat detection
Amazon GuardDuty is designed to consequently manage resource use dependent on the general movement levels inside your AWS records and remaining tasks at hand. GuardDuty includes location limit just when vital and diminishes use when the limit is not, at this point required. You presently have financially savvy engineering that guarantees you have the security handling power you need while limiting costs. You just need to pay for the recognition limit you use, when you use it. GuardDuty gives you security at scale, regardless of your size.
One-click deployment with no additional software or infrastructure to deploy and manage
With one-click in the AWS Management Console or a single API call, you can enable Amazon GuardDuty on a single account. With a few more clicks in the console, you can enable GuardDuty across multiple accounts. Once enabled, GuardDuty immediately starts analyzing continuous streams of account and network activity in near real-time and at scale. There are no additional security software, sensors, or network appliances to deploy or manage. Threat intelligence is pre-integrated into the service and is continuously updated and maintained.
How it Works